The Essential Guide to Two-Factor Authentication (2FA) for Enhanced Security
In today’s digital landscape, securing your online accounts is paramount. Two-Factor Authentication (2FA) provides an additional layer of security beyond passwords, significantly reducing the risk of unauthorized access. In this comprehensive guide, we’ll walk you through everything you need to know about 2FA, from its importance to practical implementation.
What is Two-Factor Authentication (2FA)?
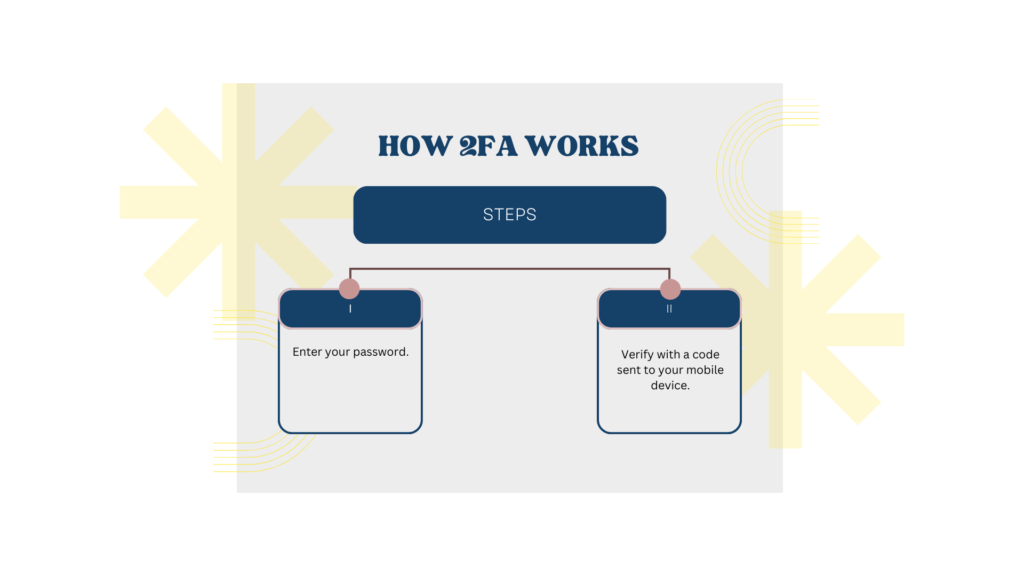
Two-factor authentication is a security process that requires users to provide two different authentication factors to verify their identity. Typically, it combines something you know (like a password) with something you have (such as a code sent to your mobile device) for added security.
Why is 2FA Essential?
In an era where cyber threats loom large and data breaches are prevalent, relying solely on passwords for account security is no longer sufficient. Here’s why integrating Two-Factor Authentication (2FA) into your digital practices is crucial:
Enhanced Security Beyond Passwords: Passwords, no matter how strong, can still be compromised through various means like phishing attacks, data breaches, or brute-force attacks. 2FA acts as a second line of defense, significantly reducing the likelihood of unauthorized access even if passwords are stolen or guessed.
Mitigates the Risk of Unauthorized Access: With 2FA, an additional verification step (like a one-time code sent to your phone) is required along with the password. This means that even if someone manages to obtain your password, they would still need access to your secondary authentication method, significantly reducing the risk of unauthorized entry into your accounts.
Protection Across Various Devices: 2FA is not restricted to just one device; it extends its security across multiple devices. Whether accessing your account from a new computer, smartphone, or tablet, 2FA ensures that the user’s identity is confirmed through an additional factor beyond the password.
Compliance with Industry Security Standards: Many industries and regulatory bodies recommend or require the implementation of 2FA to ensure a higher level of security compliance. Adhering to these standards not only protects your data but also helps maintain trust with clients or users who prioritize secure practices.
Prevents Account Takeover: Account takeover (ATO) attacks are on the rise. Hackers target accounts to steal personal information, financial data, or even impersonate individuals for malicious purposes. 2FA acts as a robust defense, reducing the success rate of such attacks.
User-Friendly Security Measure: Despite providing an additional layer of security, 2FA is relatively easy to set up and use. Most platforms and services offer user-friendly options for enabling 2FA, making it accessible to a wide range of users.
Setting Up 2FA: Step-by-Step Guide
Setting Up Two-Factor Authentication (2FA): Step-by-Step Guide
- Facebook:
Go to Settings: Click on “Settings & Privacy” > “Settings.”
Security and Login: Select “Security and Login.”
Two-Factor Authentication: Find and click on “Use two-factor authentication.”
Follow the Prompts: Choose the desired method (like text message or authenticator app) to receive codes and follow the prompts to activate 2FA.
- Google (Gmail):
Sign-in & Security: Visit your Google Account settings.
Security Section: Navigate to “Security” > “Two-step verification.”
Enroll in 2FA: Click on “Get started” and follow the instructions to set up 2FA using options like text messages or Google Authenticator.
- Twitter:
Profile & Settings: Click on your profile picture > “Settings and privacy.”
Account: Go to “Account” > “Security.”
Enable Login Verification: Check the box for “Login verification” and follow the prompts to set up 2FA.
- LinkedIn:
Account & Settings: Click on “Me” > “Settings & Privacy.”
Account Security: Go to “Account” > “Security” > “Two-step verification.”
Turn On 2FA: Choose “Turn on” and follow the steps to set up 2FA.
- Additional Tips:
Authenticator Apps: Consider using authenticator apps like Google Authenticator or Authy for generating 2FA codes. They’re more secure than SMS-based codes.
Backup Codes: Generate and safely store backup codes provided by platforms. These can be used to access your accounts if you lose access to your primary 2FA method.
- General Advice:
Regularly Review Security Settings: Check your security settings periodically to ensure 2FA is active and up-to-date.
Keep Recovery Options Updated: Add alternative recovery options to regain access to your accounts if needed.
Conclusion: Protect Your Accounts Today!
Enable Two-Factor Authentication on your accounts and take a proactive step towards bolstering your online security. Safeguard your sensitive information and enjoy peace of mind in the digital realm.
At Forward Edge Consulting Limited, we are committed to empowering users with robust cybersecurity practices. Stay tuned for more insightful content on protecting your digital presence.
